Research staff:
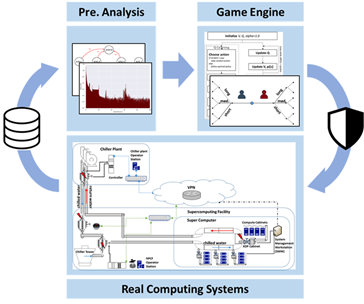
We investigate the use of game-theoretic approaches for response to ongoing attacks. The aspect of automated response is understudied, since data-driven analysis is typically adopted for attack detection, whereas the response upon detection still relies heavily on human decisions. We find game-theoretic models to be a good fit in terms of designing automation methods for security response. In our model, we abstract the attacker and the defender into two players, each deciding his/her next moves based on the payoff resulting from advancing or stopping the attack, respectively. The figure below provides an overview of our approach, in which we collect data from real systems (cyber-physical systems, Web servers, etc.) to understand the operation of the target system and the behavior of the attackers. A preliminary analysis of the data has enabled us to formulate the interaction of the adversaries into a game-theoretic model. We propose an optimal strategy in which variations of the game-theoretic algorithms, reflecting varying assumptions and game settings, are used to provide the best security for a system under the assumptions and restrictions defined in the game. Further, we expand the definition of the attacker’s behavior and his/her possible actions by applying advanced machine learning techniques from the attacker’s perspective. We are exploring the possibility of attacks with self-learning features, and studying the feasibility of current detection/response methods.
From real security data to game theory.