Research staff:
Probabilistic graphs for intrusion detection
We investigate methods for preemptive detection of suspicious activities from compromised user accounts. We use probabilistic graphical models, and, in particular, factor graphs. Factor graphs improve expressiveness and subsume classical probabilistic graphs, such as Bayesian networks and Markov random fields. The graphical models are being automatically extracted from over 8 years of security logs of real incidents collected at the National Center for Supercomputing Applications at the University of Illinois. The incidents include credential stealing, remote code execution, and abuse of infrastructure to send spam and launch denial-of-service attacks.
To preemptively detect attacks before the delivery of attack payloads, we have built a prototype intrusion detection system called AttackTagger. It uses factor graphs to construct probabilistic graphs of attacks and perform inference on attack progression. To make AttackTagger available to the community, we have integrated it into the Bro IDS (https://www.bro.org/), whose team actively collaborates with us.
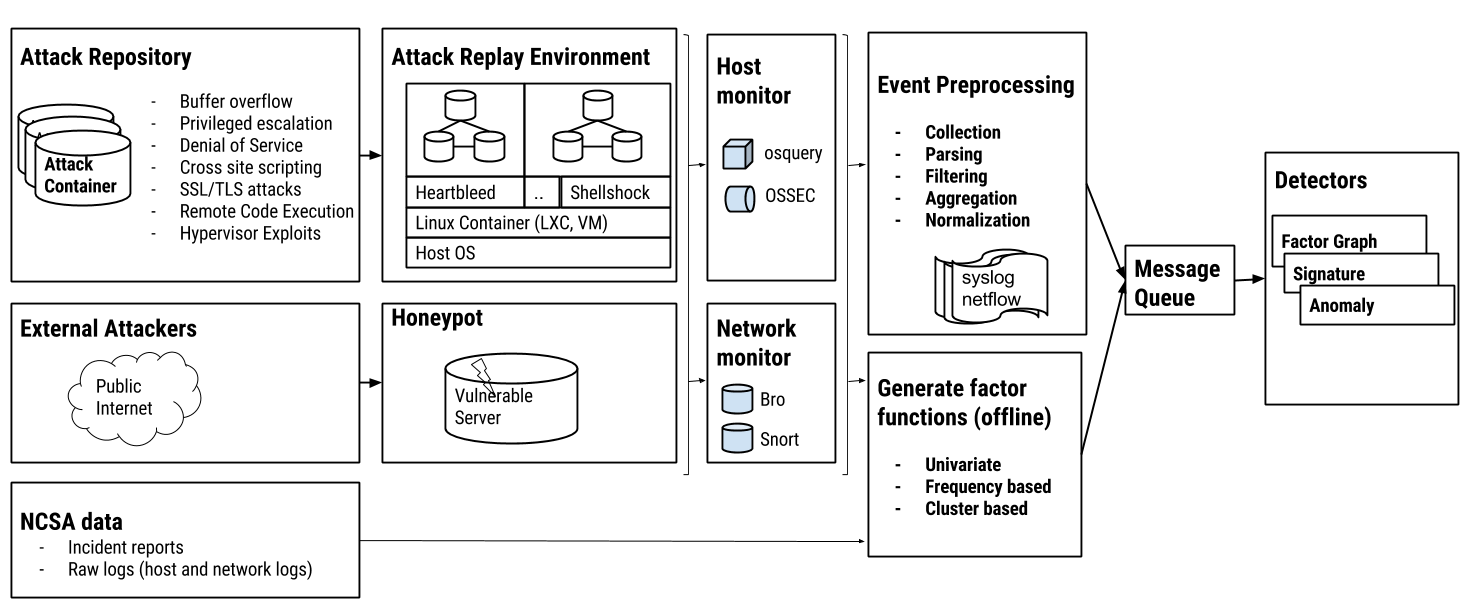
To assess the accuracy of AttackTagger and train the models, we have built a comprehensive testbed composed of (i) tools to replay past incidents; (ii) a honeypot to observe the behavior of real attackers against decoy servers, and (iii) Docker containers equipped with exploit codes and vulnerable software to recreate realistic attack scenarios. Figure 1 shows an example of the testbed.
Workflow of attack analysis, detection, and simulation.